Let's Play Uplink
<< | ^^ | >>
Let's Play Uplink
Uplink is a hacker simulation made by the ever-creative Introversion Software. It's not really about what hacking is actually like - instead, it's a simulation of extra-dramatic hollywood-style hacking.
Let's go mold the digital world in our own image!
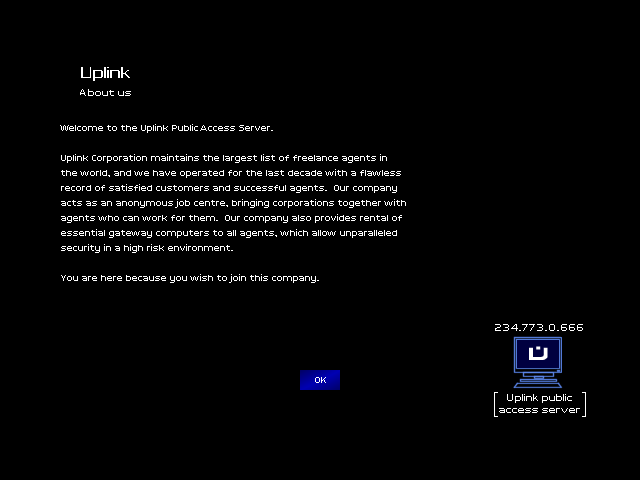
This sounds like what I'm looking for!
Time to resgister as a new agent.
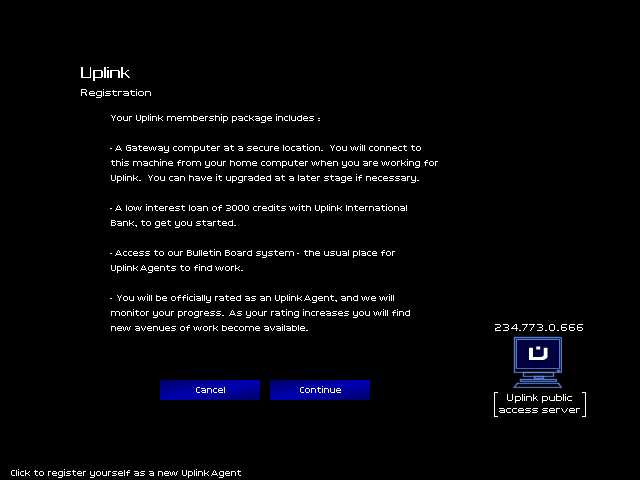
As a new Agent, I get:
-Cash!
-A PC!
-Access to missions!
-A rating!
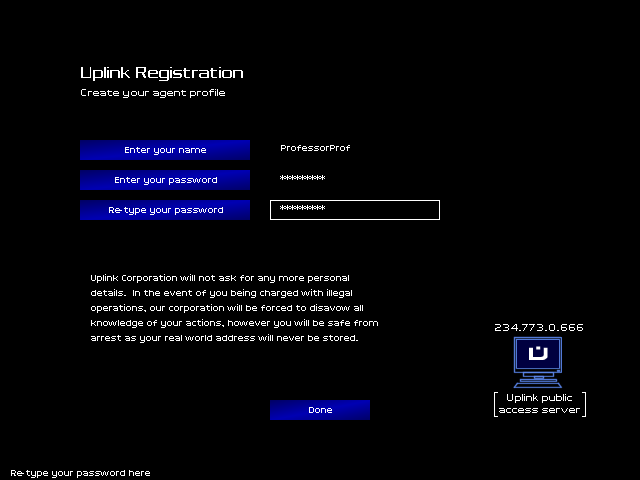
Creating my new login.
Username: ProfessorProf.
Password: Swordfish.
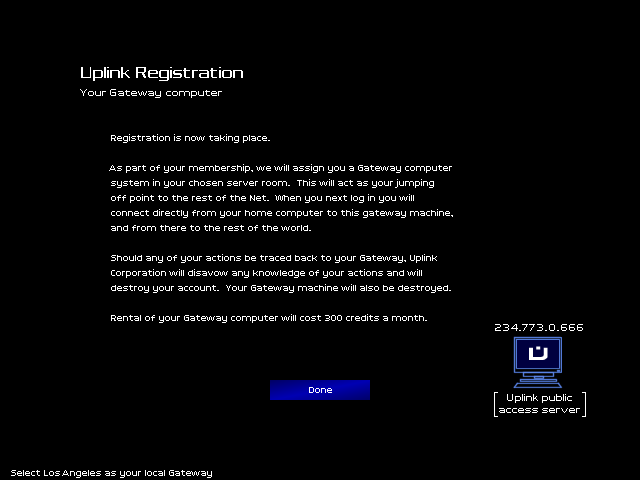
The golden rule: If I get caught, Uplink never knew I existed.

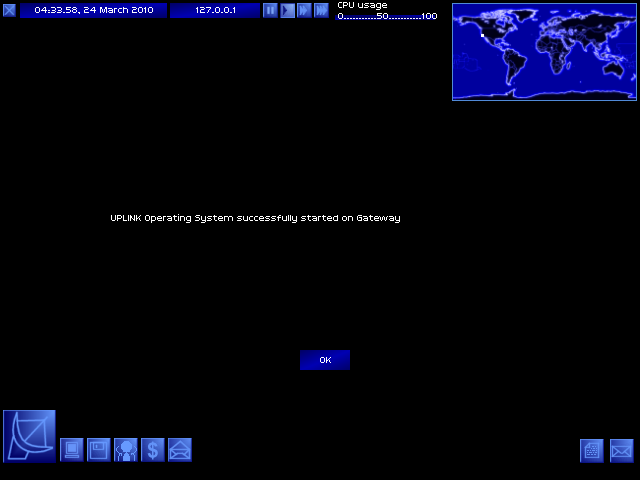
Chapter 1: Welcome to Uplink
And I'm connected to my Uplink terminal!
Let's take a look at what I've got.

Hardware!
60 Ghz processor, 1 Gigaquad per second bandwith, and a 24 Gq hard drive.
For the FUTURE YEAR OF 2010, this is a pretty basic machine.
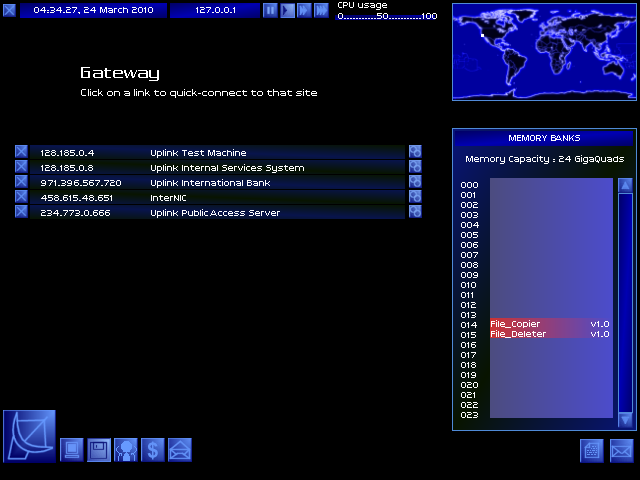
My file system!
I only have two files, both of them programs: File_Copier and File_Deleter. These are important, as without them I can't move files around.
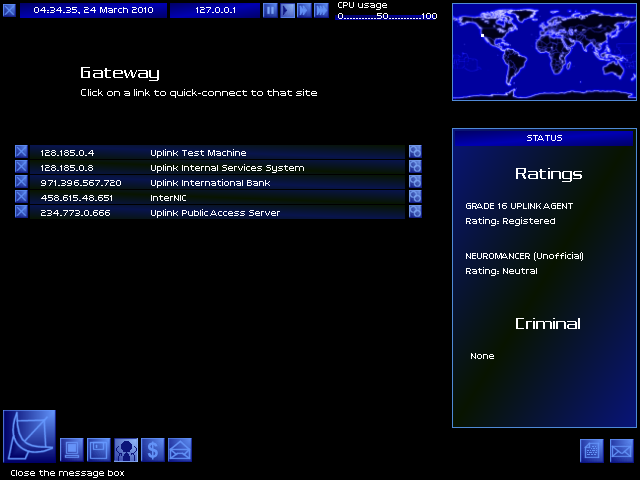
Rating!
My UPLINK AGENT rating is Registered, the lowest rating on the ladder.
NEUROMANCER rating is the closest thing Uplink has to an alignment system. It ranges from dangerous revolutionary to unstable psychopath.
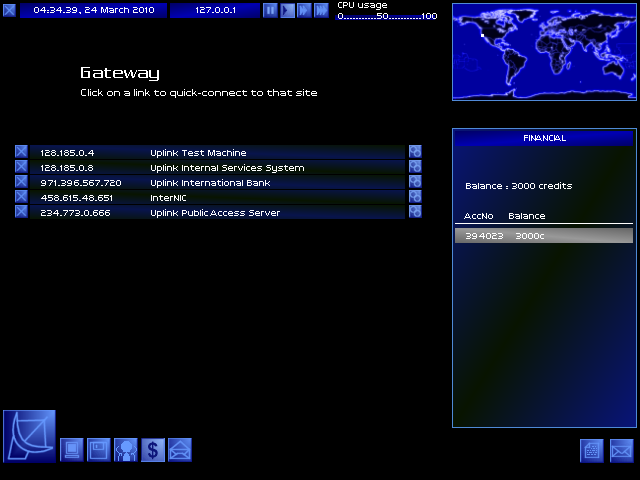
Money! I have one bank account, with 3000 credits (borrowed) in it.
On the left is remote servers I know about:
Uplink Test Machine: Soon to be relevant.
Uplink Internal Services System: Where I go to interact with the Uplink organization - get missions, buy software or hardware, etc.
InterNIC: A free-to-use database of internet information. I'll be making good use of this.
Uplink Public Access Server: The server I connected to to register as an agent.
On the bottom right, I have two emails!
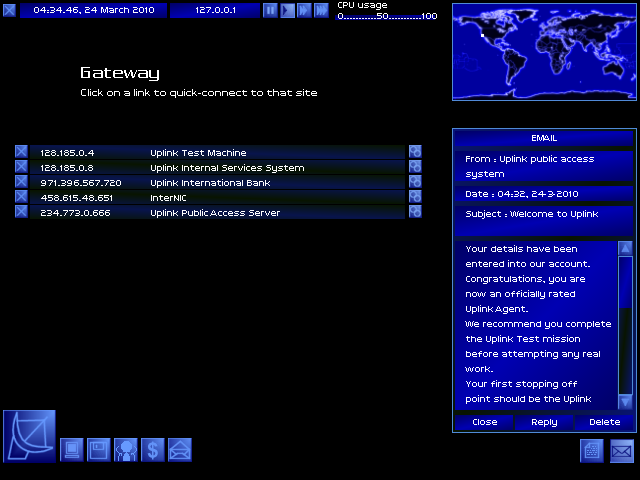
The first one is a "Welcome to Uplink" message! Boring, delete.
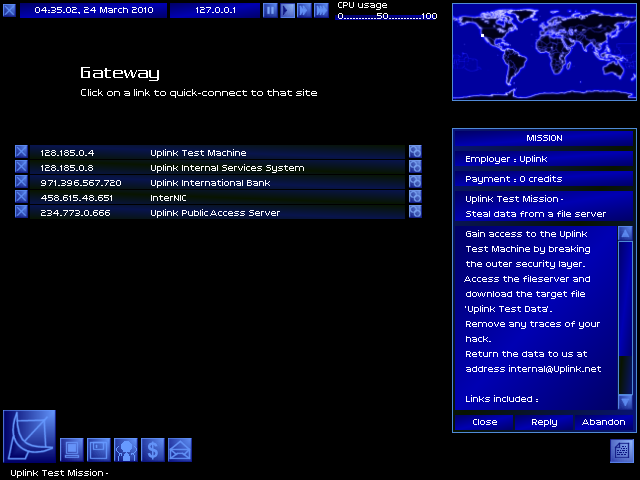
The second is my first mission! A test I have to pass in order to accept other missions.
Employer: Uplink
Target: Uplink Test Machine
Objective: Steal the file 'Uplink Test Data'
Payment: 0c
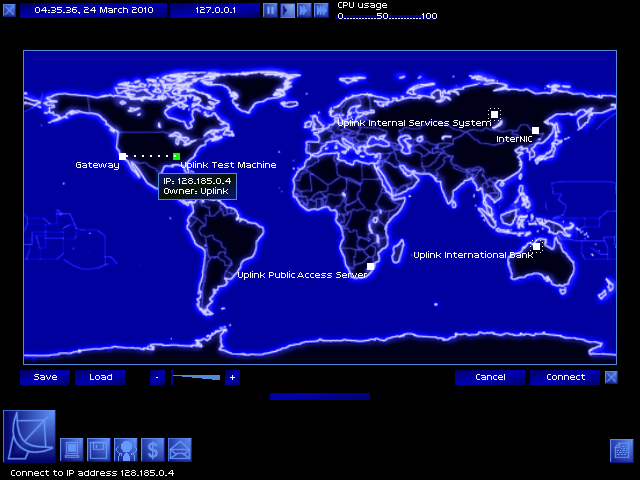
World map! This will soon be suffocatingly crowded, but it's still important.
Green dots are systems I have missions targetting; systems with dotted borders are systems that I have legitimate accounts on. The Gateway is the computer that Uplink has provided for me - it's in Los Angeles.
Dotted line is my connection path. Let's connect!
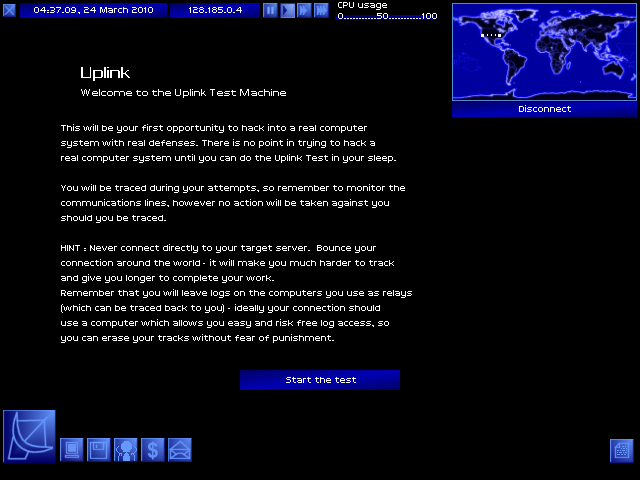
Goal: Get in, get file, get out.
LET'S START THE TEST

...It's our first obstacle! A password.
I don't know the password. At this point, my progress is stonewalled. I have nothing I can do but guess randomly, or disconnect.
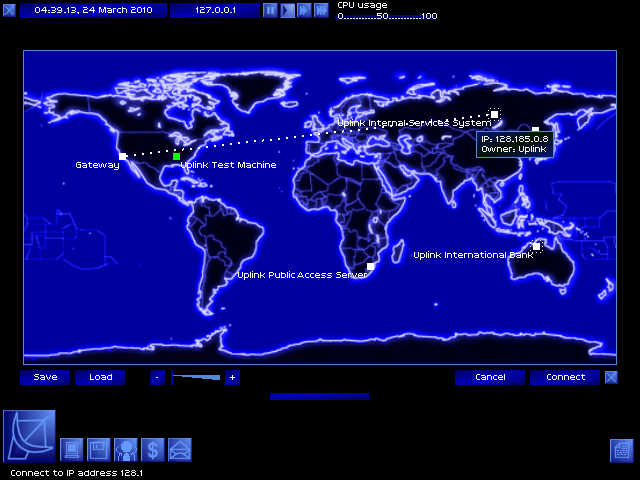
I choose the latter!
TIME TO CHECK OUT UPLINK INTERNAL SERVICES
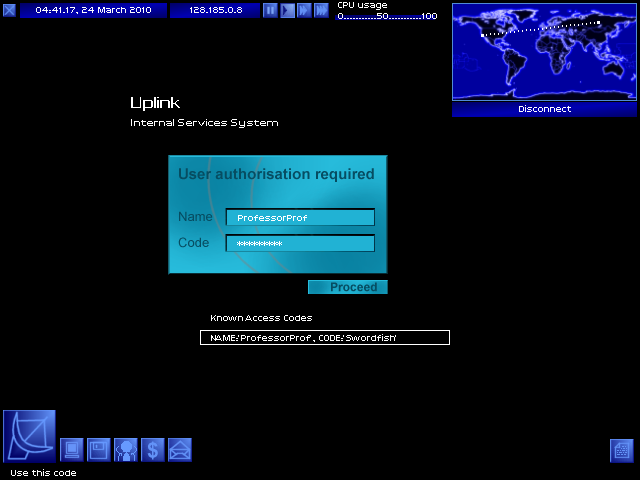
This time, I actually have a functional user/pass combo! Because I belong here.
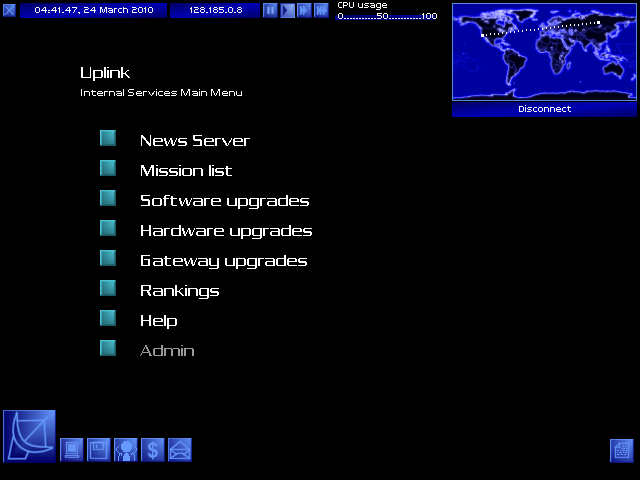
Lots I can do here! For now, though, I'm only doing one thing.
To software upgrades!
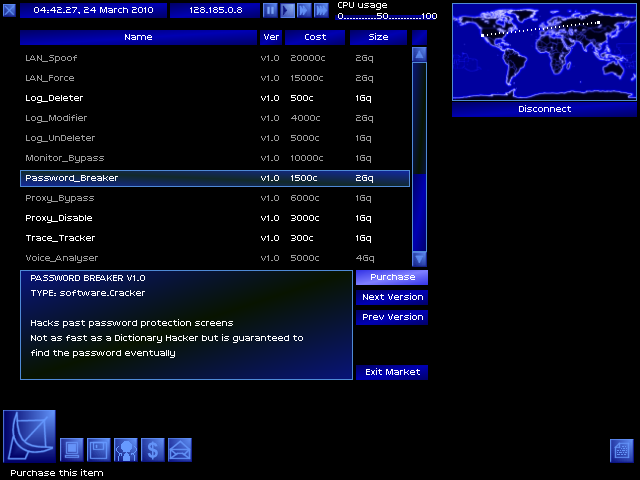
This should do the trick!
Buying this and Trace_Tracker v2.0, totalling 2100 of my 3000c.
BACK TO THE TEST SERVER
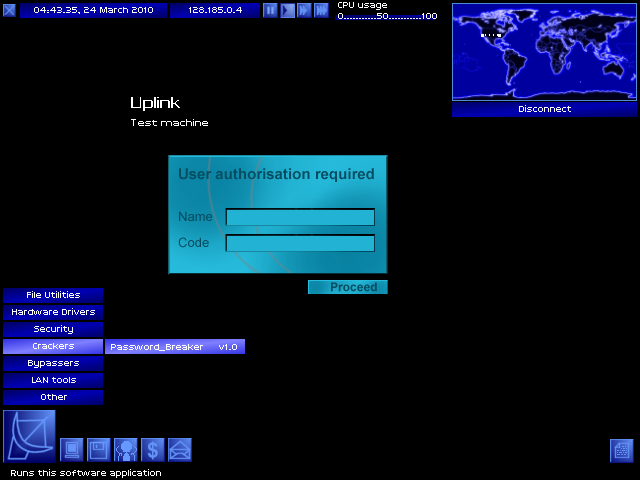
Now I have a new program to run!
SELECT PASSWORD_BREAKER, CLICK ON PASSWORD FIELD
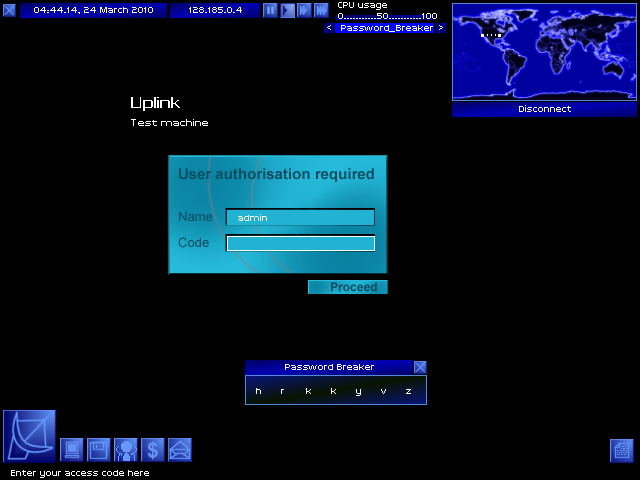
When running, Password Breaker decyphers one letter of the password every few seconds - the exact speed depends on my computer and the target system's security.
The letters flick by randomly, but one is cracked, followed by--
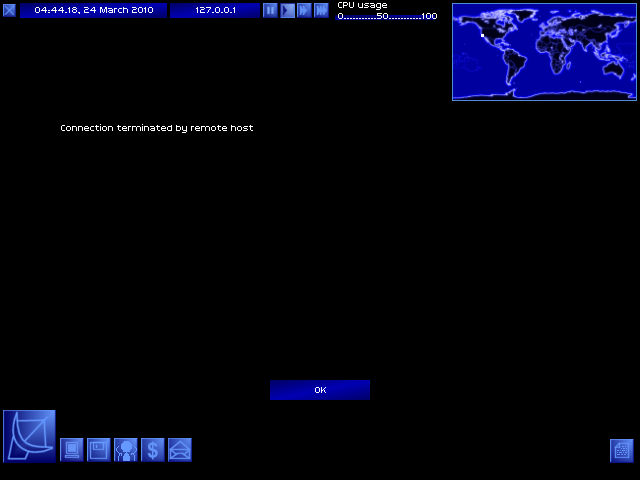
HEY

A downside of Password Breaker is that as soon as you begin the crack, the target system starts tracing the connection. When it figures out where you're coming from, it shuts down the connection - and against real systems, this could result in major fines, criminal records, or even being hunted down by the FBI.
This is my first line of defense - bouncing calls through several intermediate systems! This way, when they trace the connection, they'll see the Uplink Internal Services System, and then have to trace again to find InterNIC, and so on... it gives me much more time to do what I'm there to do.
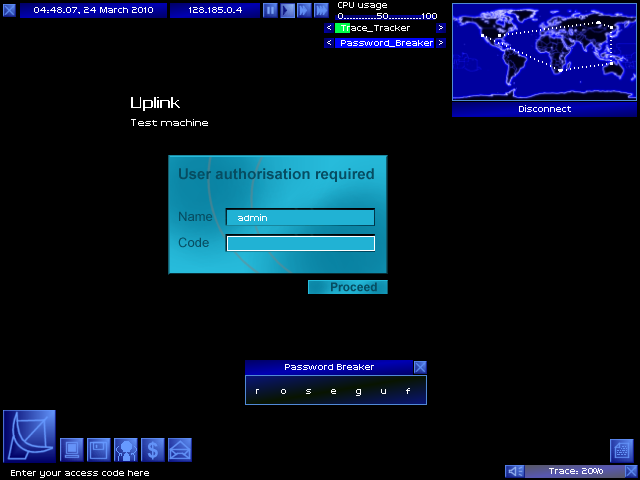
Round 2! Several things at work here.
At the bottom right, you can see the other program I bought - Trace_Tracker! v1.0 just lets you know when your connection is being traced, but I have v2.0, which also tells you what percentage of your connection path has been traced.
At the top center, you can see my list of active programs! With the arrows there, I can change how much CPU I'm dedicating to each program - I've bumped Password Breaker up to almost 100%, to break the password faster.
Lower center: Password Breaker is doing its job!
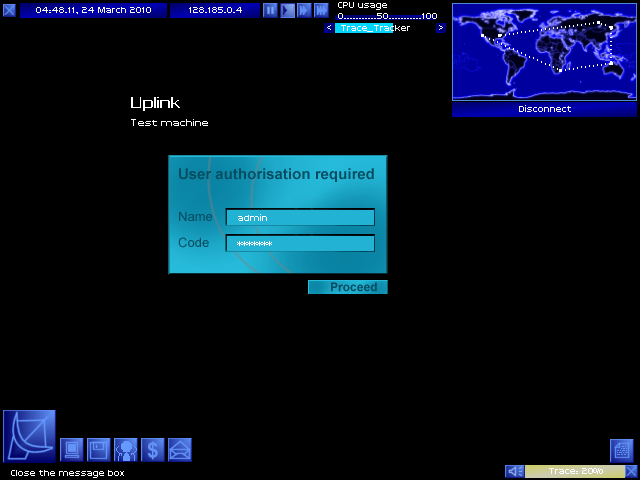
Password cracked! It was 'rosebud'.
It's actually always rosebud, meaning that metagamers can beat this mission without buying any software at all.
In we go!
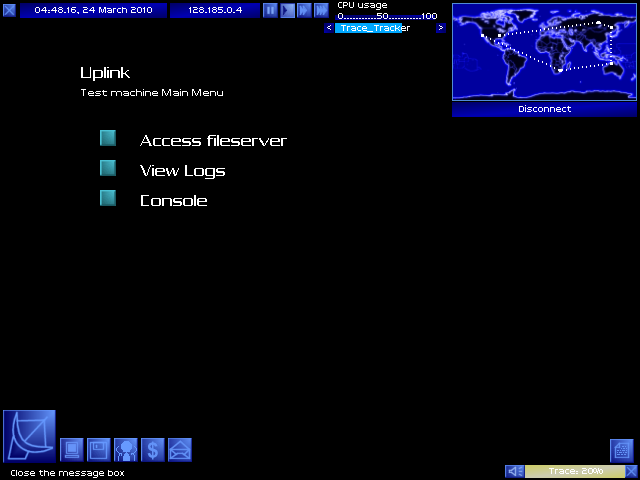
Here we are! What we want is in the fileserver.
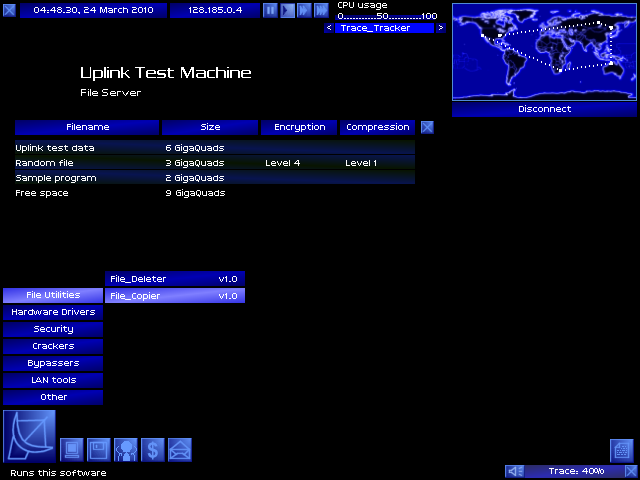
Target identified!
GO GO GADGET FILE_COPIER

The server has traced back through two jumps of my five-jump connection chain! DOWNLOAD FASTER.
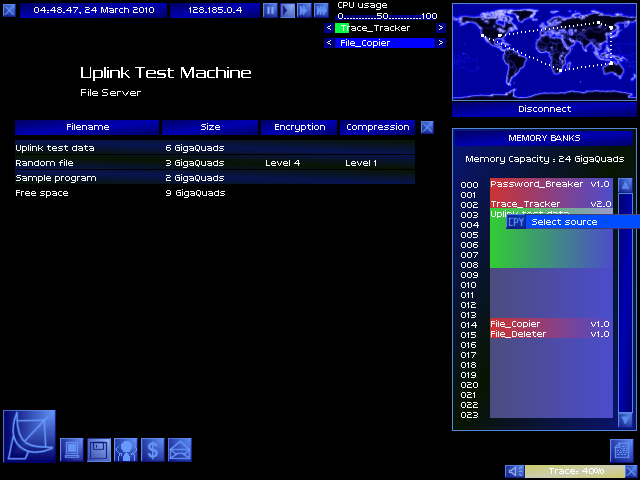
File obtained!
CUT CONNECTION
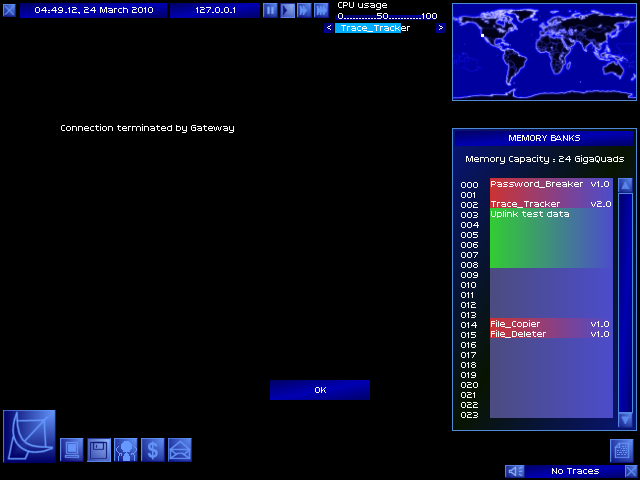
Success!
If this were a real mission, there would be followup now - such as the password I used to connect being revoked, or having to take action to prevent a long-term investigation from tracking me down days later.
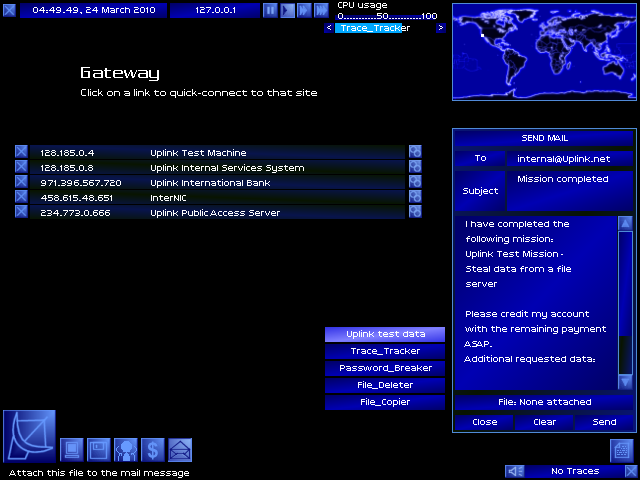
Now to send a reply to the mission, attaching the target file, and I'm done with the mission!
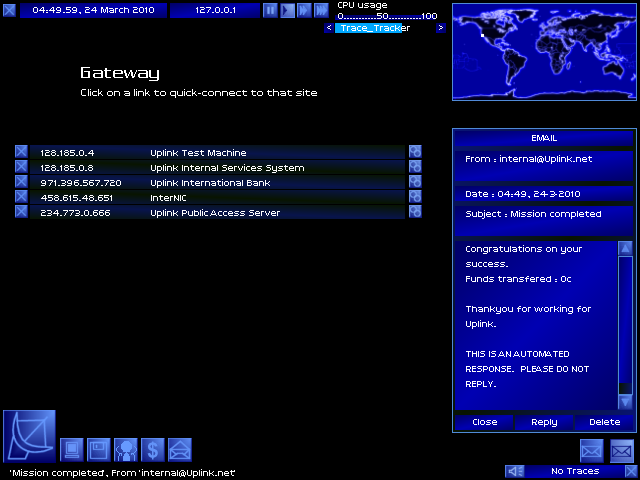
I get two messages as a result!
The first is the standard mission success message, letting me know that I have been rewarded with 0 credits.
The second is an advance in UPLINK RATING
Uplink Echeladder
????????
????????
????????
????????
????????
????????
????????
????????
????????
????????
????????
????????
????????
????????
Beginner
Registered
Next time: Earning some cash!
<< | ^^ | >>